Dragnet - Your Social Engineering Sidekick
Because this system has so many moving parts, things may not "just work" until later versions. It is recommended to watch this repo so that you're notified when new versions are pushed. Big features like automated infrastructure deployment are coming soon.


- WooCommerce, Analytics, Google Analytics">
- Complain
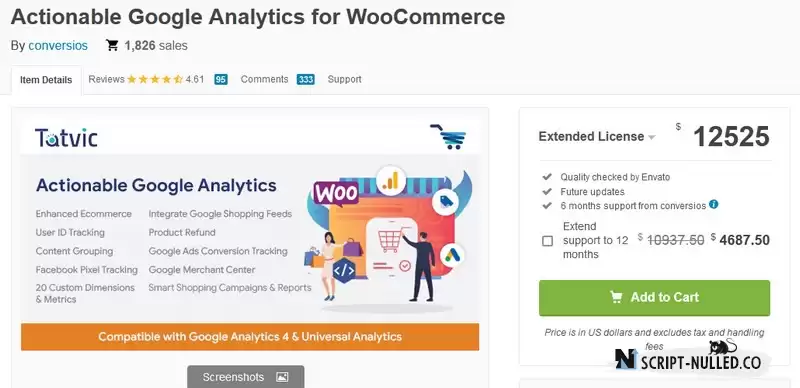
Actionable Google Analytics for WooCommerce
Actionable Google Analytics for WooCommerce v.4.1.0 Actionable Google Analytics for WooCommerce is a plugin that integrates your WooCommerce store with Google Analytics in just 5 minutes. NO CODING REQUIRED.

Changing your voice ?
Changing your voice ? People often change their voice on audio recordings — to preserve anonymity or just to make fun of friends. For example, to say something frightening in the voice of a monster.


? Maltego blog. Up-to-date tools, modules and manuals.
? Maltego blog. Up-to-date tools, modules and manuals. • Since June 2022, #Maltego has launched a new section on its blog, which describes relevant and useful tools, cheat sheets, manuals and modules for its tool.


Social Engineering Tool Magic-Online
Witchcraft Online is a social engineering tool with sub-functions that aim to meet people's social needs, such as social media services and short message services. Launched attacks are always associated with spam (resending messages), spoofing and brute force engineering, since dos or denial of service subfunctions are nothing more than just attracting interested users.


This is a set of social engineering techniques and payloads
This is a collection of social engineering tricks and payloads being used for credential theft and spear phishing attacks.


Tool Information Gathering & social engineering DarkSide
Tool Information Gathering & social engineering Write By [Python,JS,PHP] DarkSide


Jokes on colleagues
Help a buddy prank his colleagues! Show your mettle with spoofing emails, malicious attachments, spoofing sms, and spoofing phone calls to get access to voicemail


? true story... How I was hacked, my cryptocurrency wallets were emptied, and what Apple said.
? true story... How I was hacked, my cryptocurrency wallets were emptied, and what Apple said. • The story of how the creator of the website for job search in the field of cryptocurrencies cryptojobslist withdrew personal savings in cryptocurrency, simultaneously gaining access to Apple, Yahoo, Gmail and Telegram accounts with two-factor authentication enabled.


? true story... Christopher Rocancourt. The story of a famous conman and a $40 million fraud.
? true story... Christopher Rocancourt. The story of a famous conman and a $40 million fraud. • At one time, writers Ilya Ilfov and Evgeny Petrov created a literary image of the “great combinator” Ostap Bender, who was able to "take" money in "four hundred comparative honest ways." One of his modern prototypes is Christophe Rocancourt. The only difference is that Bender called


? true story... What are the risks of pentesters trying to hack your company. Part 1.
? true story... What are the risks of pentesters trying to hack your company. Part 1. • There have been no interesting stories from the lives of pentesters and social engineers for a long time, and to be honest, I missed this category. Today we will add another fascinating story to our list. Enjoy reading.


? true story from Group IB... False alarm.
? true story from Group IB... False alarm. • Today I found for you another and interesting story from Group IB, accepted reading:


Popular articles
New articles
Discussing

booken
in post
BetSwap99 Casino script source code
0
24 June 2025 05:20