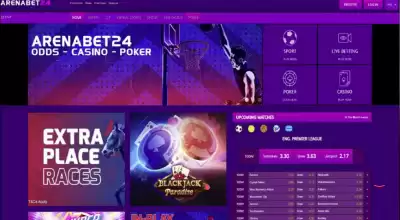
Arenabet24 betting script
Betting and casino script ARENABET24 - THE NEW HOT VERSION Betting, casino, poker and virtual sports, as well as keno and bingo. Release date 2022 NEW system! Control your own rules, choose everything with our powerful system that lets YOU actually decide everything. You have the ability to control how much people can win or not, set the rules, win percentage and you You will keep 100% of all