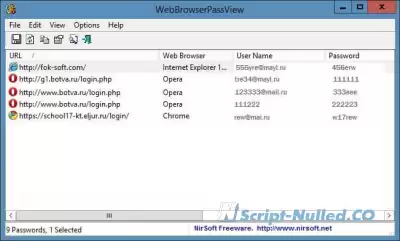
Vulnerability of cryptographic protection systems
Currently, software protection methods based on the use of cryptographic algorithms are widely used. Regarding the effectiveness of protection of this class, I would like to cite the opinion of Chris Kaspersky, author of the book "The Technique and philosophy of hacker attacks": "These defenses look unbreakable. They "look" because developers do not take into account the