Chntpw: Reset and bypass the Windows password
13-03-2022, 15:21
chntpw is a utility for viewing some information and changing user passwords in the Windows NT/2000, XP, Vista, 7 SAM user database file, usually located in \WINDOWS\system32\config\SAM in the Windows file system. In Kali Linux, it is already installed natively.
Options
Syntax: chntpw [OPTIONS] <samfile> [systemfile] [securityfile] [otherreghive]
-h This message
-u <user> Username to change, Administrator is default
-l list all users in SAM file
-i Interactive. List users (as -l) then ask for username to change
-e Registry editor. Now with full write support!
-d Enter buffer debugger instead (hex editor),
-t Trace. Show hexdump of structs/segments. (deprecated debug function)
-v Be a little more verbose (for debuging)
-L Write names of changed files to /tmp/changed
-N No allocation mode. Only (old style) same length overwrites possible
Launch Kali, fly into the directory of this file, and then open this folder in the terminal. Further:
command: chntpw –l <sam file>
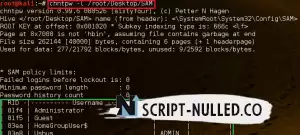
Then we have to select the username whose password needs to be changed.
command: chntpw –u <user> <sam file>
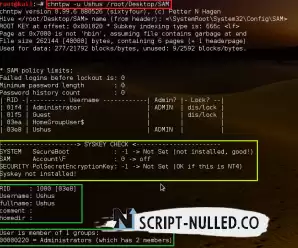
The tool will now appear in the user's edit menu.
And then we have to choose what we want to do with the account.
Just enter the number corresponding to our required tasks. Here we change the password. So, enter "2".
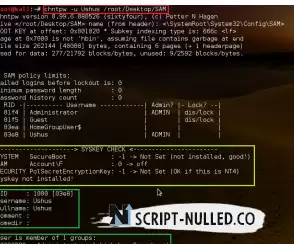
The tool will then ask you to enter a new password. Just type it in and press enter. Then it will ask if we want to save the password. Press y to save the new password. Now we have changed the password in the SAM file. In a real-world scenario, this is done by uploading a Kali Linux boot CD to a Windows system without changing the location of the SAM file.
13-03-2022, 15:21
13-03-2022, 16:02
13-02-2024, 08:14


4 comments
Information
Users of Visitor are not allowed to comment this publication.