Fibratus
16-01-2023, 14:01
Windows Spy Blocker: Protecting Windows from Espionage and Tracking overlamer1December 02, 2019
In the modern digital world, quite a lot of questions "rest" on the problem of tracking personal data, as well as a dark scheme of spying on user activity. In this article, we will talk about how you can fully protect yourself from such problems in the Windows operating system, and also consider the features of the useful Windows Spy Blocker tool.
Windows Spy Blocker Tool
Windows Spy Blocker is designed to block espionage and tracking. The application is executed using the Go programming language. This program captures and analyzes network traffic based on a set of specific tools. It is available for Windows 7 SP1, Windows 8, Windows 10.
How Windows Spy Blocker Works
In principle, it is clear that the developer wrote this executable file specifically in order to block tracking programs that are detected based on network traffic analysis. It is not Russified, and it is not necessary, since it does not have a full-fledged interface, and the program, in fact, is a set of certain rules.
The console appears immediately after the launch permission. The first thing to do is to turn on your internet connection, if it is not already turned on. If it so happens that there is no Internet connection, an error will appear. The commands are laid out on the console with a description of what each one does, so it will be easy for you to figure it out.
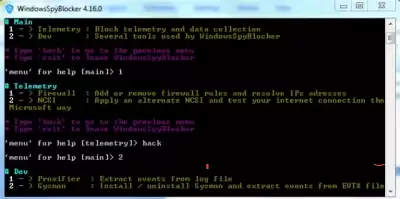 If we depict this information hierarchically, it will look something like this:
If we depict this information hierarchically, it will look something like this:
The results obtained are changed according to the entered command. So, to capture and analyze network traffic for telemetry, the developer used QEMU virtual machines on the Proxmox VE platform. At the same time, memory dumps are cleared daily, the current rules for adding or removing some hosts or firewall rules are compared. The developer indicates that he uses the following tools to capture traffic: Qemu -net dump, Sysmon, Wireshark, Proxifier. All events that occur are saved in the logs folder.
The data folder contains blocking rules based on domains or IP addresses detected during the capture process: blocking telemetry, OS updates, blocking third-party applications.
I immediately advise you to create a special folder under Windows Spy Blocker, where you initially need to save the program itself, and all configurations, logs and folders that the utility will create in the process will be saved there. The developer of the program recommends copying the hosts file created by the program and located in the Data folder and pasting it into the hosts of your system.
The utility will be in demand among those users who want to monitor their network traffic.Thus, now you will be able to fully use the wonderful Windows Spy Blocker tool with an excellent motive to help avoid tracking and acceleration. Its functionality is very easy to use, so in the course of its conscientious work, it is unlikely to disappoint you.
16-01-2023, 14:01
16-01-2023, 12:32
29-01-2023, 11:03


There are no comments
Information
Users of Visitor are not allowed to comment this publication.