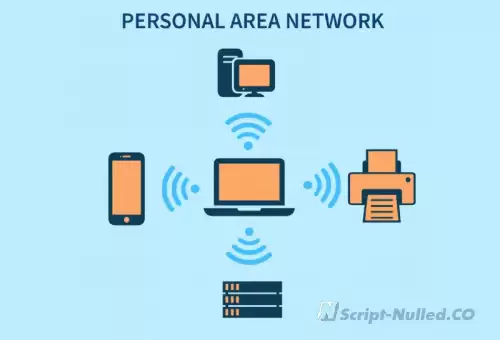
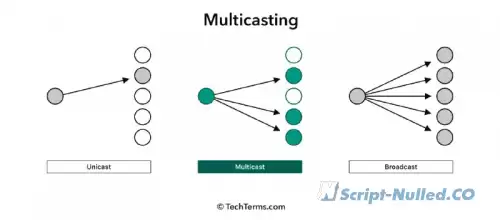
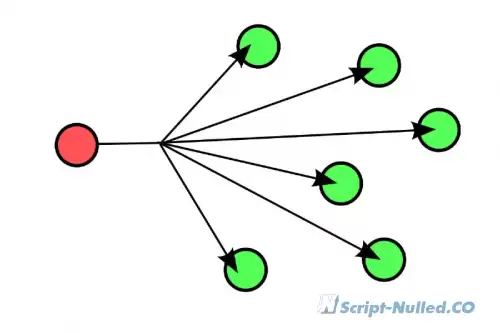
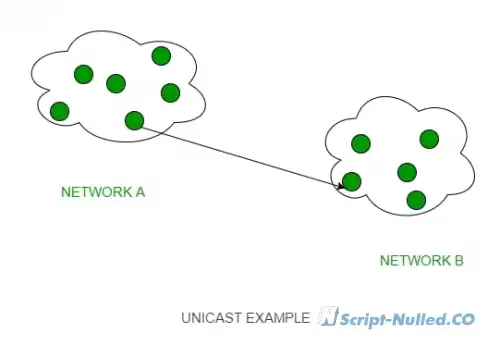
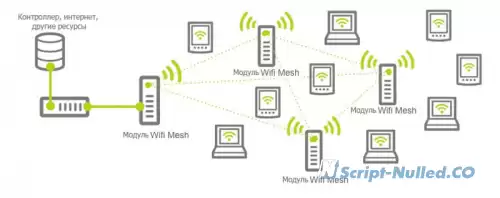
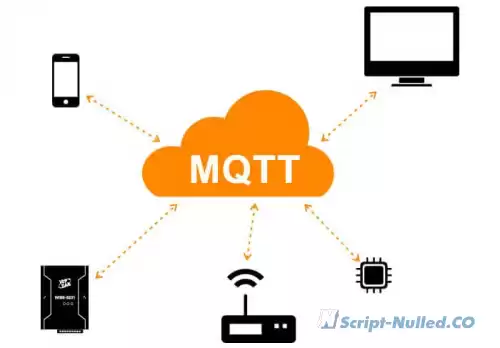
What is PAN? • A personal network (PAN) is a network built "around" a person. PAN is a computer network that is used to transfer data between devices, such as computers, phones, tablets, etc. Personal networks can be used both for information interaction of individual devices with each other, and for connecting them to higher-level networks, for example, the global Internet, where one